From monolithic to containerised architecture
Application maintenance for FREEDOM Giuseppe Gangemi
Services
- Maintenance
Technologies
- AWS
- AWS RDS
- Docker
- Terraform
- Amazon Aurora MySQL
- AWS SDK
- Amazon Cloudwatch
About the client
FREEDOM Giuseppe Gangemi is a global fasteners and assembly solutions supplier. The company specialises in providing services related to glass production and processing industries. GlassCad is an application created to assist customers in the designing and planning of glass spaces. It allows for the optimisation of the ordering process and for improvement to the cutting and machining of glass. The software leverages advanced algorithms and CAD technology to generate efficient cutting plans. This minimises waste and maximises material utilisation with advanced care of the optimal selection of fittings and auxiliary materials.
Application maintenance – project goals
The primary goals of the project were to:
- Migrate the AWS application from ‘eu-central-1’ region to ‘eu-west-1’
- Move the application from a monolithic architecture to a containerised architecture
- Improve the scalability and availability of the application
- Reduce infrastructure costs
- Implement a development, staging, and production environment
- Implement a content delivery network (CDN) to improve performance and reduce latency
- Implement a managed database solution for the application
- Implement AWS Secrets Manager to securely store and retrieve sensitive application data
- Implement AWS Certificate Manager to manage SSL/TLS certificates for the application
Project steps
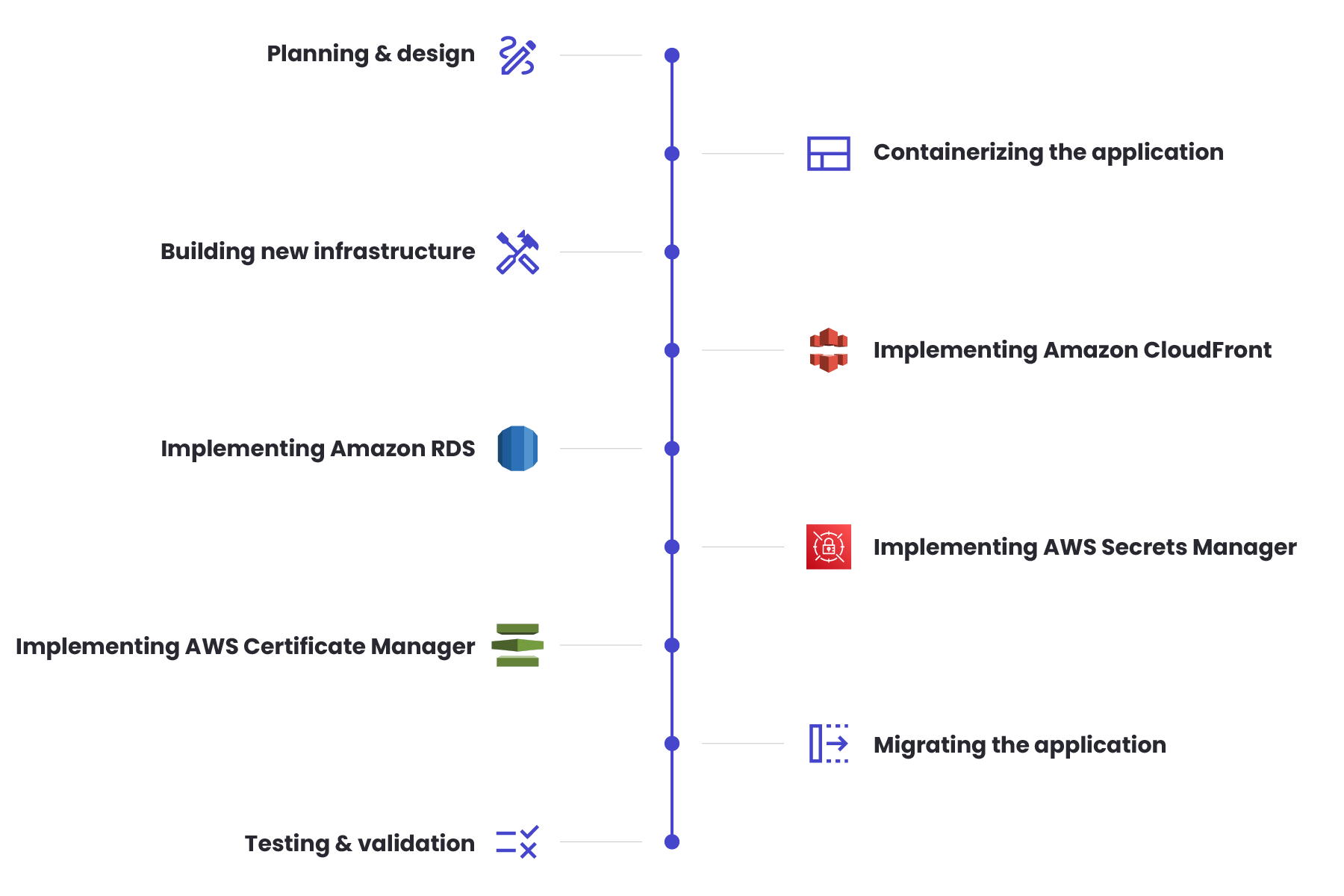
- Planning and design
The first step was to plan the migration and design the new architecture. This involved the analysis of the existing application, identifying components that could be containerised, and the creation of the new infrastructure on AWS. The team decided to use Amazon Elastic Container Service (ECS) to manage the containers, Amazon CloudFront as a CDN to improve performance and reduce latency, and Amazon Relational Database Service (RDS) as a Managed database solution for the application. They also decided to implement AWS Secrets Manager to securely store and retrieve sensitive application data and AWS Certificate Manager to manage SSL/TLS certificates for the application.
- Containerising the application
The next task was to containerise the application. It involved breaking down the monolithic application into smaller components that could be managed and scaled independently. The team used Docker to containerise the application components and created images for each component so that they could be stored in Amazon Elastic Container Registry (ECR).
- Building the new infrastructure with Terraform
With the containers ready, the team began building the new infrastructure on AWS using Terraform. We created separate Terraform modules for the development, staging, and production environments, each with its own VPCs, subnets, load balancers, auto-scaling groups, ECS clusters, and RDS instances.
- Implementing Amazon CloudFront
Once the new infrastructure was in place, we implemented Amazon CloudFront as a CDN to improve performance and reduce latency. We also created a CloudFront distribution for each environment and configured it to cache frequently accessed content, such as images and static files.
- Implementing Amazon RDS
The next step was implementing Amazon RDS as a managed database solution for the application. We created RDS instances for each environment and configured the databases to use Amazon Aurora, which is a highly available and scalable database engine. Because of that, our team also configured the security groups and access controls to ensure that the databases were secure.
- Implementing AWS Secrets Manager
The team then implemented AWS Secrets Manager. As a result, it allowed us to securely store and retrieve sensitive application data such as database credentials, API keys, and other secrets. AWS SDK was used to programmatically access the secrets from the application and implemented fine-grained access controls to ensure that only authorised users could access the secrets.
- Implementing AWS Certificate Manager
AWS Certificate Manager was introduced to manage SSL/TLS certificates for the application. We used ACM to generate SSL/TLS certificates for each environment and configured the load balancers and ECS services to use the certificates for secure communication with the application.
- Migrating the application
Once the new infrastructure, CDN, databases, Secrets Manager, and Certificate Manager were in place, it was time to begin migrating the application from the old infrastructure to the new one. We used a rolling deployment strategy to gradually deploy the new containers and validate the application’s functionality after each deployment. Also, AWS CloudWatch helped to monitor the application’s performance and availability and implemented auto-scaling to ensure that the application could handle increased traffic.
- Testing and validation
After the migration was complete, our team conducted extensive testing and validation. It was necessary to ensure the application was functioning correctly in the new environment. That is why we also conducted extensive load testing to validate the application’s ability to handle the expected traffic volume and load.
Process
Results
We completed the application maintenance project successfully, and the new infrastructure met the goals of improving scalability, availability and reducing infrastructure costs. The use of containers and auto-scaling allowed the application to handle increased traffic and load, while the use of AWS Secrets Manager and Certificate Manager helped to also improve the security of the application. The implementation of AWS CloudFront also enhanced the application’s performance and reduced user latency. Finally, using Terraform allowed for easy management and deployment of the infrastructure across multiple environments, and simplified the entire application stack’s control, which fulfilled Mr. Gangemi’s need for a streamlined replication process.
Case Studies
See our other success stories
CONTACT