Cloud computing security 101: what are the risks?
Once seen as an addition to the on-premises data storage solutions, the cloud as a technology has changed a lot since 2002 introduction of Amazon Web Services. It’s estimated that the global spend on cloud services will reach $474 in 2022 with cloud revenue to surpass estimate non-cloud revenue for enterprise IT markets in the next few years and 85% of organisations adopting the cloud-first principle by 2025.
This unprecedented usage growth for the cloud technology comes at a price, though. Ability to share and access data from anywhere in the world has enabled global businesses to operate and thrive – especially during the Covid-19 pandemic – but it also brought a swarm of cybersecurity risks and issues with 74% of large US companies experiencing a data breach in the last 12 months.
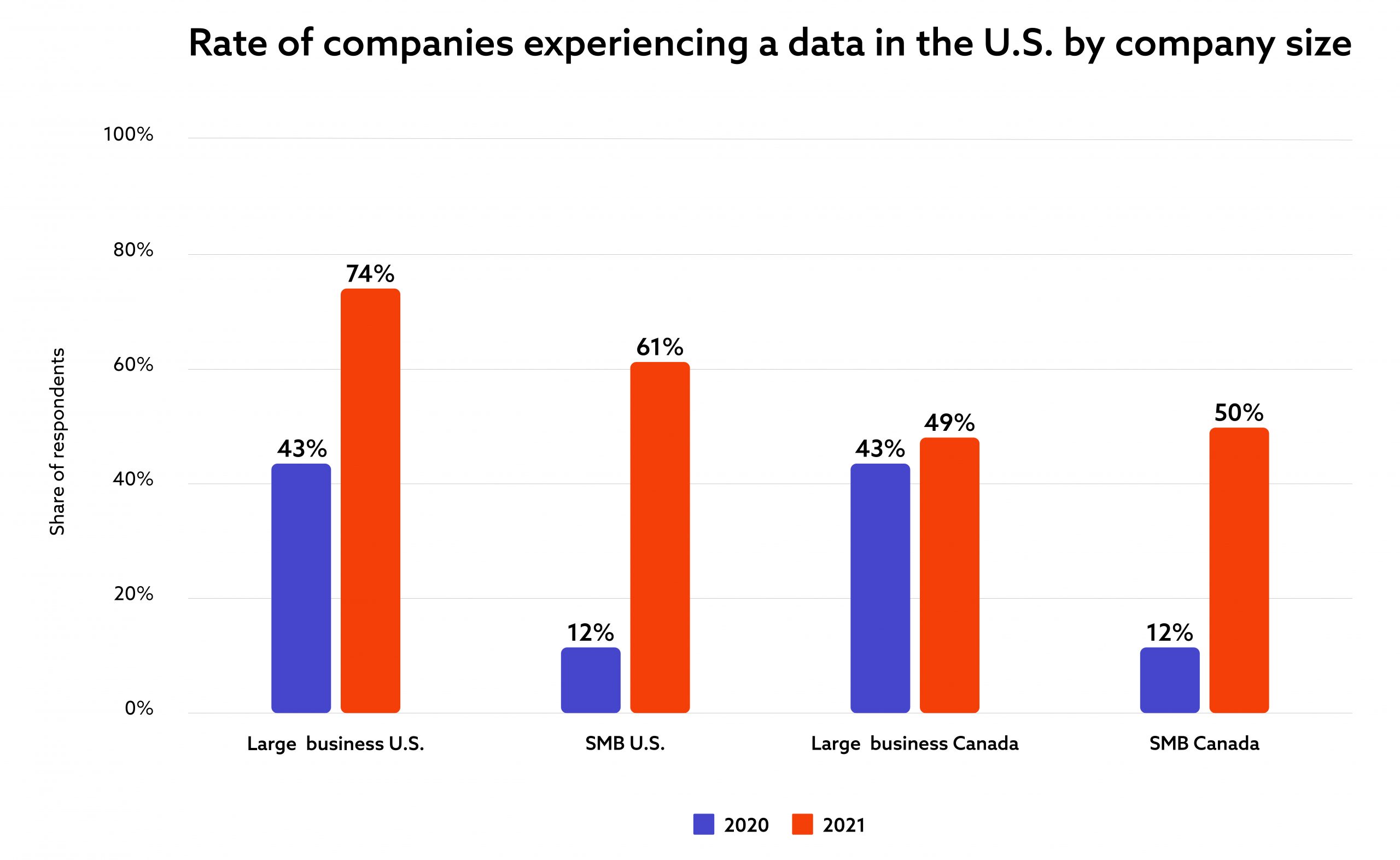
What are the main reasons for that and how business can make themselves more resilient to cloud security fails?
Let’s check how secure is the cloud technology supplied by the providers.
How secure is the cloud?
In short: it is very secure.
Similarly to other cloud providers, Amazon Web Services now offers full compliance and certification aligned with sector-specific standards such PCI-DSS, GDPR, HIPAA, SOC 2, and many others. The cloud providers have also been continuously implementing solutions and tools that avert or mitigate security threats. They also conduct and are subjected to regular and comprehensive maintenance and security audits as they are – unsurprisingly – interested in the longevity and the reliability of the services. Cloud providers such as AWS (Amazon Web Services) and Azure build secure tools and it is now up to us – their regular users – to use them safely.
In this article, I’m exploring the topic of the cloud computing security risks. I will also feature actionable advice on how to address these risks from two of our cloud experts: Tomasz Wojciechowski, a newly appointed Head of Cybersecurity at Spyrosoft and our Head of Cloud Engineering, Lukasz Marcinek.
What are the risks of cloud computing?
As you may assume from the introduction, the higher risk level for businesses looking to use or maintain their cloud solutions lies in the so-called ‘human factor’ rather than the lack of reliability from the providers – data shows that 95% of cloud security fails are due to this factor.
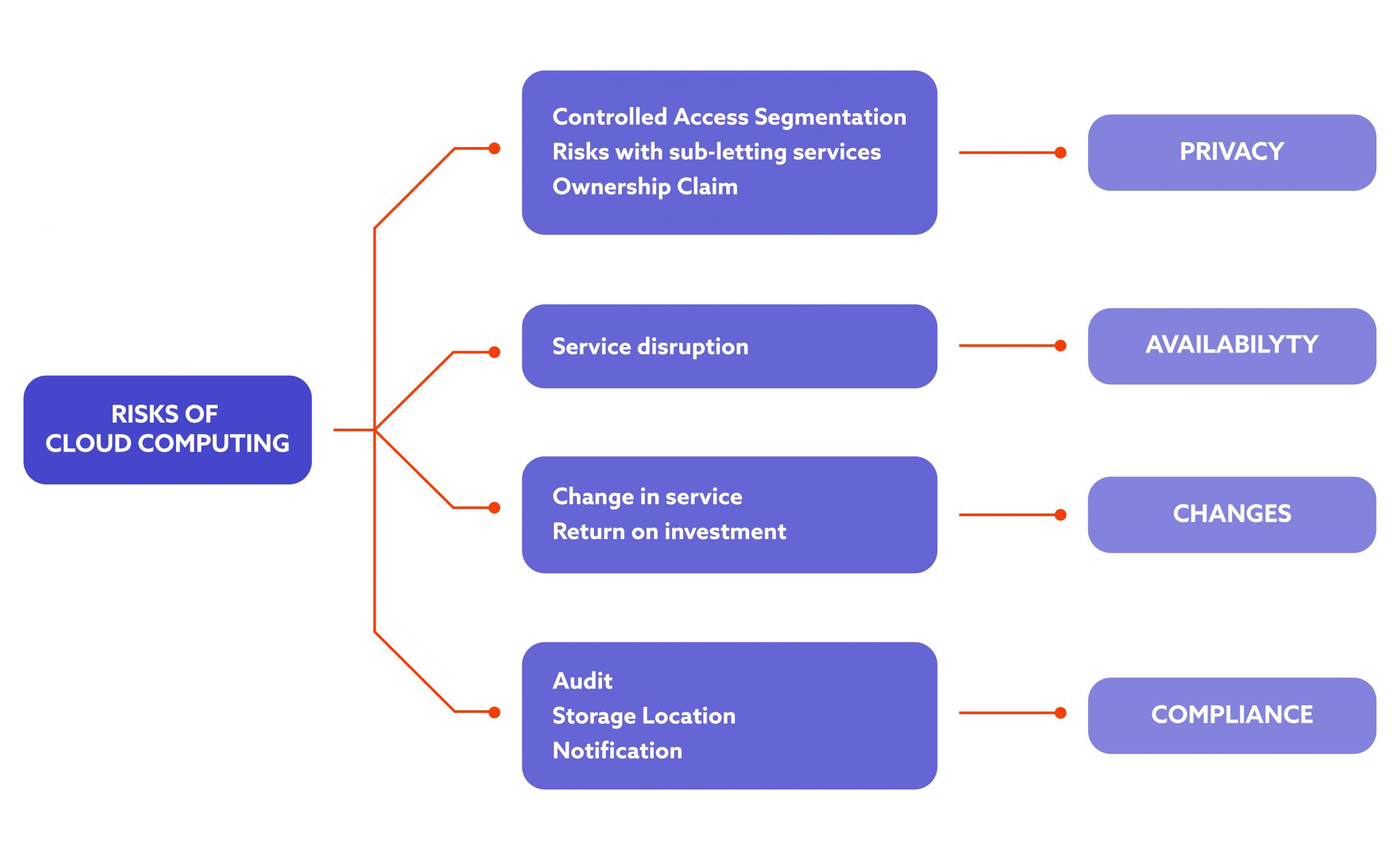
Data security fails
If you look at this issue, the most important question is who has access to your company data and to what extent. Hackers look for a vulnerability low-hanging fruits and the aspect of access management is overlooked at most companies.
With multiple users and several cloud environments to manage, making sure that there are no gaps can be difficult, especially for large organisations that use on-demand services with their own systems and tools. To put it simply: if your data is unciphered, shared with many users at once across multiple cloud platforms and not monitored, it is not safe.
Compliance issues
As stated above, most of cloud providers are compliant and offer certificates for industry-wide data management norms. The services themselves may be secure but it does not mean that you should not worry about internal standard compliance. Make sure that you see compliance as an organisation-wide issue and conduct regular checkups or even use third-party bodies to assess the level of compliance for all your resources, be it internal and external.
Lack of multicloud management strategy
Managing multiple cloud solutions at once is not an easy task. If you work at a large global organisation that combines Amazon Web Services with Google Cloud and Microsoft Azure in its projects, developing a procedure on how you will approach the use of such a complex combination is necessary. In this Gartner report on cloud migration, 81% of companies stated that they already work with two or more cloud providers.
Non-authenticated API access
While using Application Programming Interfaces (APIs) for both external suppliers and your employees will help keep data in sync and automate their processes, this can also mean that your business will be more vulnerable to cyber attacks. Implementing a web application security system, adequate authorisation as well as authorisation protocols will ensure that your data is and stays secure.
Not enough cybersecurity experts
If you have ever tried to hire a cybersecurity specialist, you may be aware of this but let us state it one more time: there is a global shortage in cybersecurity professionals.
As ISC discovered in their research, there are currently 3.12 million unfilled cybersecurity roles worldwide. The sector is poised to be the fastest growing tech sector with employment growth rate of 31% in US only according to the data collected by the US Bureau of Labor Statistics. If your organisation is already struggling with this global issue, invest in internal educational schemes and upskilling your employees to ensure that you have enough resources to protect your company data.
Tenants’ separation control issues
According to Tomasz Wojciechowski, the risk of such a breach is low and although it can happen that is not something that occurs very often. It is worth mentioning nevertheless as tenants’ separation control issues can pose a serious threat to medium-sized and large organisations when many users have access to the same cloud-based resource. Failure to maintain separation between multiple tenants can lead to a vulnerability that – in turn – can be easily spotted and exploited by hackers.
How to mitigate or avert these risks?
So, what are the actions that you can take to mitigate or averts these cloud computing risks? Here is a list of best practices from our experts, Lukasz Marcinek and Tomasz Wojciechowski.
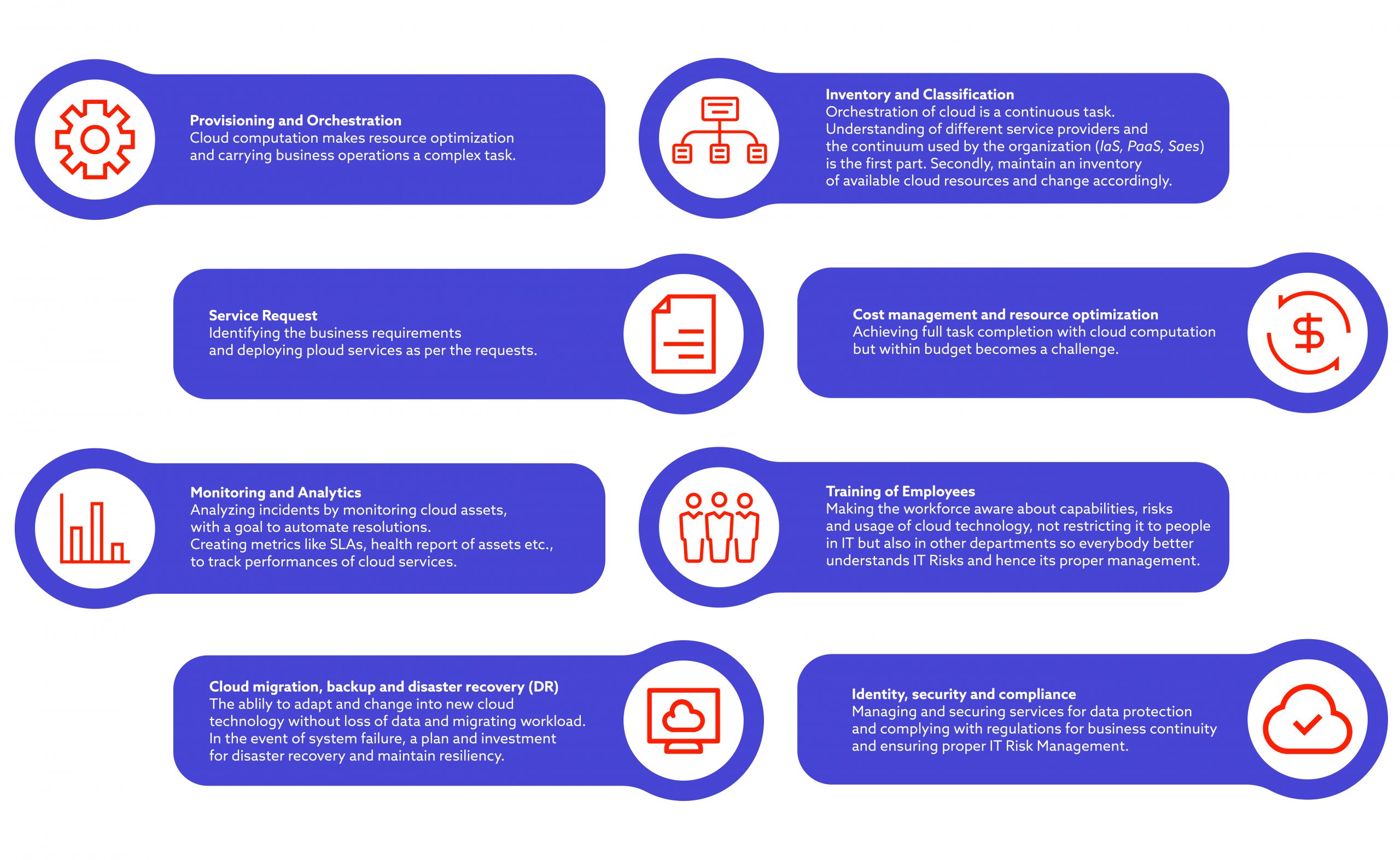
Train your team
Using unencrypted file sharing, easy-to-crack passwords and personal hardware such as laptops and mobile phones for work as well as phishing attacks are among the most common missteps made by employees at smaller and larger organisations.
To ensure that your teams will not fall into these traps, conduct regular training sessions and implement regular reminders for potentially hazardous tasks. Regular compliance audits and industry-specific safety standards training may also be necessary.
Use Cloud Access Security Brokers (CASBs)
This reinstates the previous points mentioned above but it is something that is not highlighted enough in the enterprise world, according to our Head of Cybersecurity, Tomasz Wojciechowski. Cloud Access Security Brokers (CASBs) are security policy tools that are implemented to serve as a layer between cloud service users and cloud service providers. Encryption, tokenisation, malware detection, authentication and logging are all examples of such tools.
Monitor and manage your data
According to our Head of Cloud Engineering, Lukasz Marcinek, if you give access to any cloud-based resources to any of your employees or contractors, use Principle of Least Privilege. The PoLP is when a user gets the minimum level of access or permissions to complete their work tasks. The so-called ‘privilege creep’ where most or all users get full permissions and unlimited access to all resources is a bad practice.
Follow Cloud Adoption Framework
Every cloud provider has its own Cloud Adoption Framework – including Microsoft and AWS – and it will be helpful in planning your migration to cloud, your security strategy and even naming your resources. Start by developing your security end state and work from there by mapping to concept and frameworks, assigning roles – with ‘zero trust’ policy ingrained in the assignment roadmap – and drive the change on a business and organisational level.
Develop a risk management strategy
I’m mentioning it last but developing a sustainable risk management strategy is no small feat, especially in highly regulated sectors such as Automotive and Healthcare. Depending on your business and organisational goals, you may need to employ a few different risk management tools and techniques, including risk data quality assessment and probability and impact matrix, to build a strategy that will support your company in the long run.
Also read: How we approach risk management at Spyrosoft
Over to you
If you interested in our cybersecurity services or have a project you’d like to discuss, do not hesitate to contact our team via our Cybersecurity website or directly on LinkedIn.
About the author




