PENETRATION TESTING SERVICES
We will evaluate the security of your website, server, or application
Ensure your organisation is well protected against cyberthreats, that potential vulnerabilities are addressed, and that due diligence is performed on data security.

HOW WE CAN HELP
Cybersecurity tests are more crucial than ever
We can test the security posture of web applications, mobile applications, infrastructure, APIs, and fat clients. We use highly customisable processes depending on agreeable scope, goals, rules of engagement and exemptions. Always in line with credited standards such as OWASP, enriched with current market-driven trends and recent exploits.
We cover the complete process from initial discussions with clients through technical demo calls to penetration testing execution and comprehensive reporting.
Key benefits of Penetration Testing
Ensure your organisation is well protected against cyberthreats, potential vulnerabilities are addressed, and due diligence on data security is performed.
Improved security posture
Penetration Testing shows the organisation’s current security posture and allows potential breach points identification. It also helps to ensure that configuration management practices are correctly followed.
Identification of vulnerabilities
Identification of security vulnerabilities and listing potential threats due to real hackers’ threat simulation exercises targeted at web applications, infrastructure, mobile apps, APIs and fat clients.
Compliance with industry requirements
Industry or legal compliance requirements may dictate a certain level of Penetration Testing. Regular use of these tests shows due diligence on data security and helps to avoid challenges that can be associated with non-compliance.
Penetration testing for Automotive
Ensure your automotive systems meet the highest cybersecurity standards with expert penetration testing that identifies and mitigates vulnerabilities.
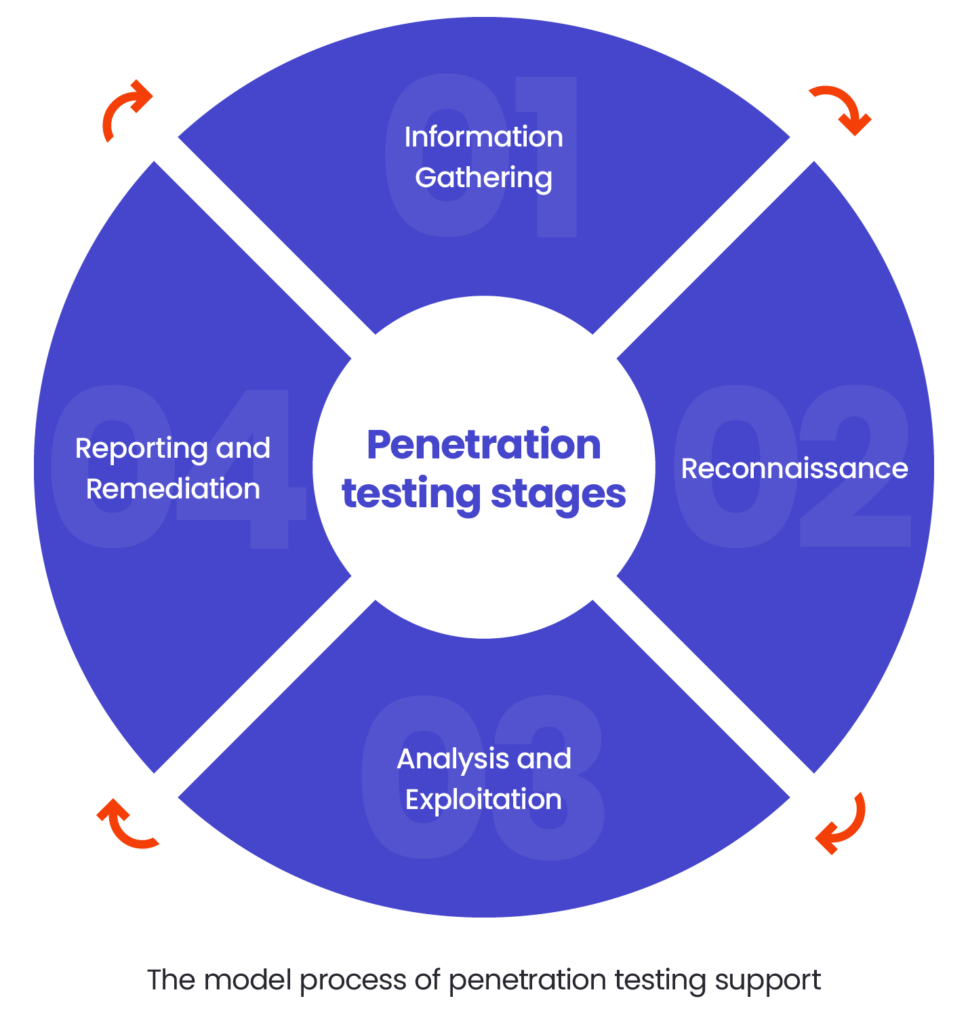
CASE STUDY
Expert guidance all the way
Challenge
Our global client needed support in the end-to-end Penetration Testing process as the company struggled with a lack of qualified professionals in their internal team. We were asked to deliver multiple Penetration Test activities on web applications, mobile applications, fat clients and infrastructure.
Solution
We worked hand in hand with the client in a Team Extension model, providing our knowledge and experience of penetration testing services.
The process involved testing such items as:
- web and mobile applications
- APIs
- infrastructure
- fat clients
We covered the transformation at every stage: from initial discussions with client representatives and technical demo calls to Penetration Testing execution and comprehensive reporting.
20%
50k +
$3.8 million
Our views and news on Cybersecurity
Contact